Now that the OUs (Operational Units), users, and groups are set up, there is an access problem that needs to be addressed. Currently, any user on the network can log in to any machine using their credentials. This means that Wolf Wallstreet from the Sales department could log in to Tina Johnson’s machine in the HR department using his login information. This is a serious security concern. If an attacker were to obtain the credentials of any employee, they could use them to gain access to any department’s machines. For example, if they managed to acquire Wolf’s credentials, they could log in to a Development team’s computer and potentially escalate their privileges to access sensitive resources like the web server. This broad access could lead to unauthorized data exposure, system tampering, or other malicious activities that compromise the integrity and security of the entire network.
To mitigate this risk, it is crucial to implement policies that restrict user logins to only their designated departmental machines. This way, each user can only access the computers they are authorized to use, significantly reducing the potential for unauthorized access and enhancing the overall security of the network.
I’m going to show how to do this using the Sales OU and Group Policy Management. Open the Group Policy Management Console again by selecting it under the tools menu:
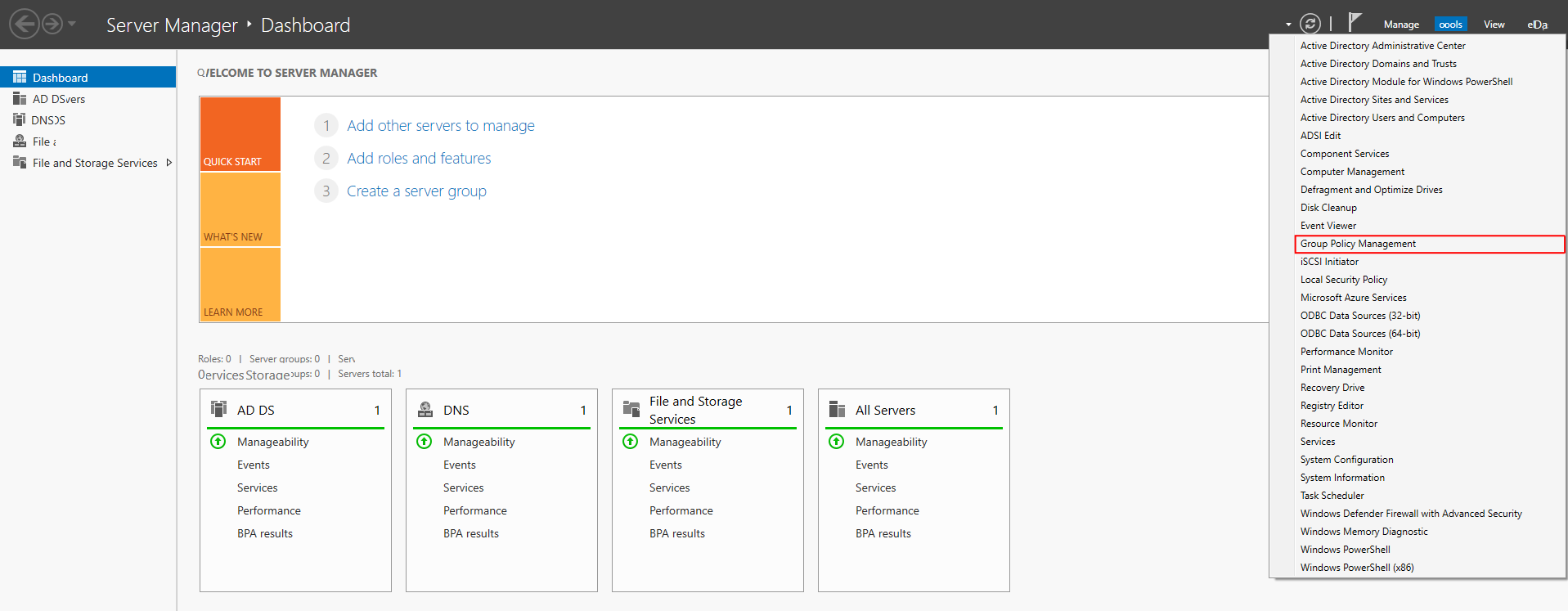
Right-Click on the Sales OU and select ‘Create a GPO in this domain, link it here’:
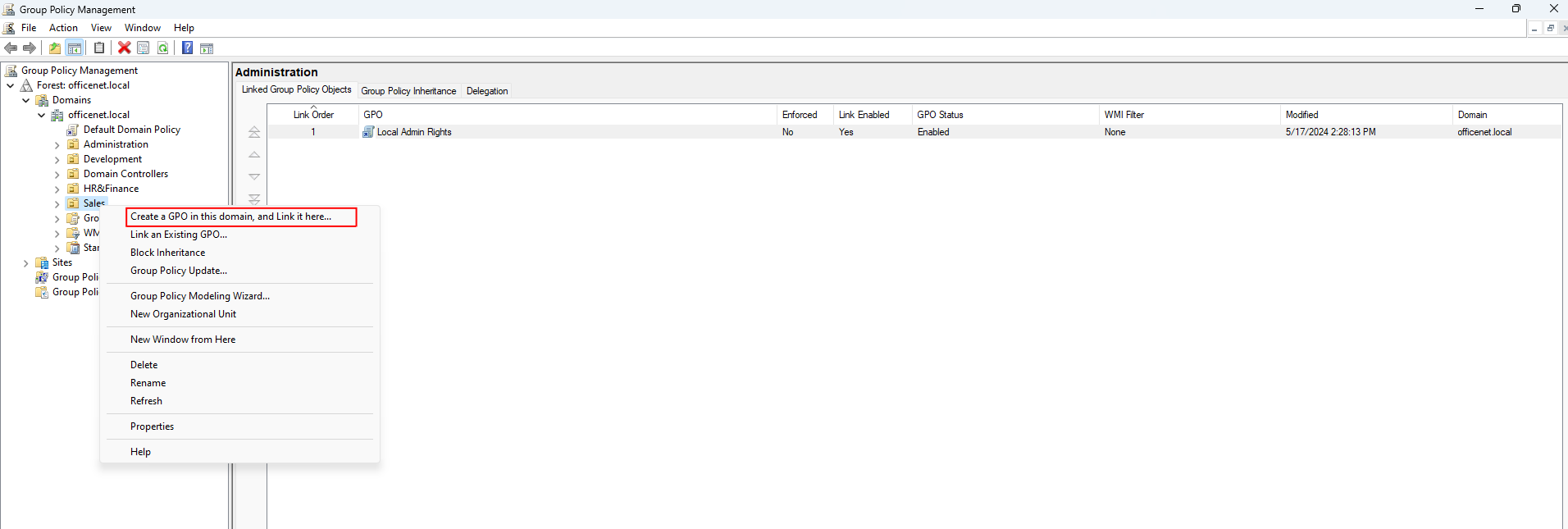
Name the policy. I’ll name this one Sales_Restricted_login:
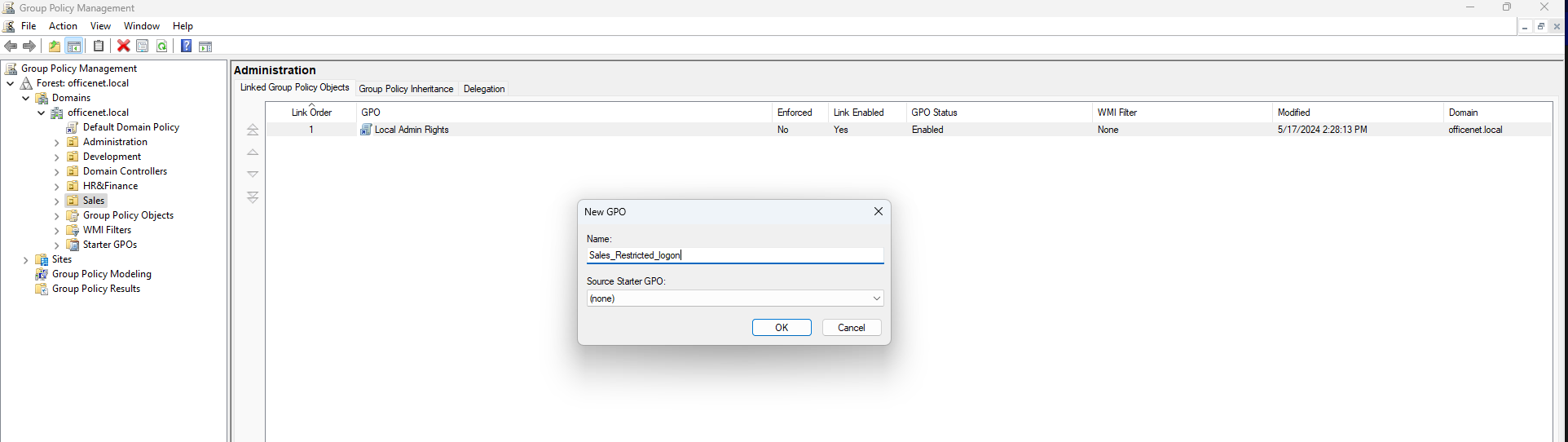
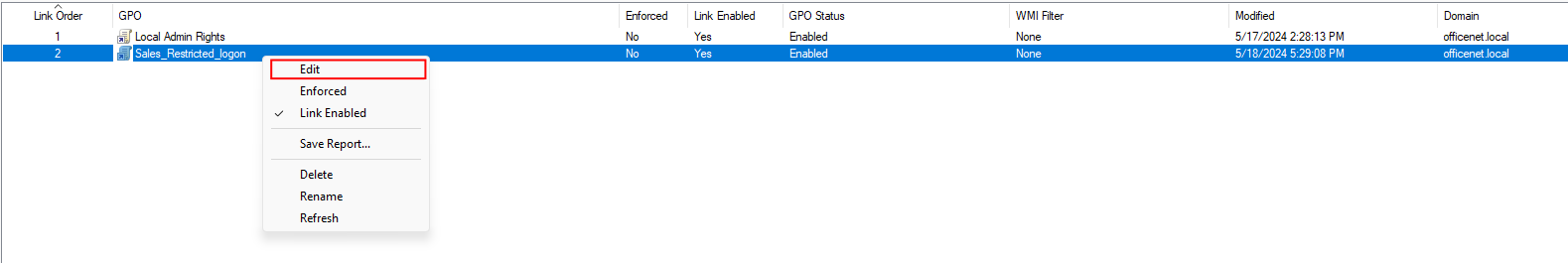
Click OK and then right-click on the policy and select edit”
In the Group Policy Management Editor select Computer Configuration > Policies > Windows Settings > Security Settings > Local Policies > User Rights Assignment:
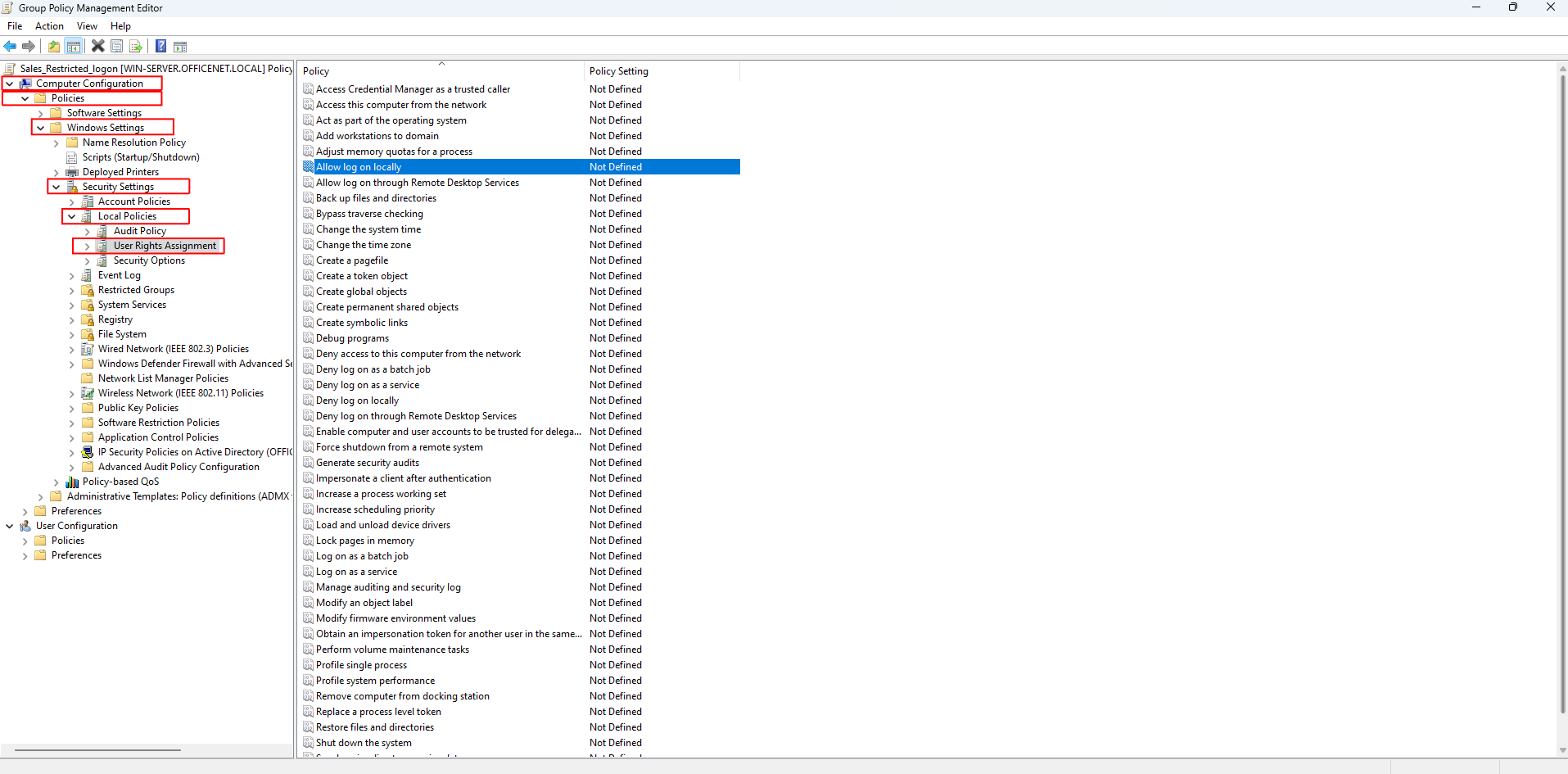
Double-click on ‘Allow log on locally’:
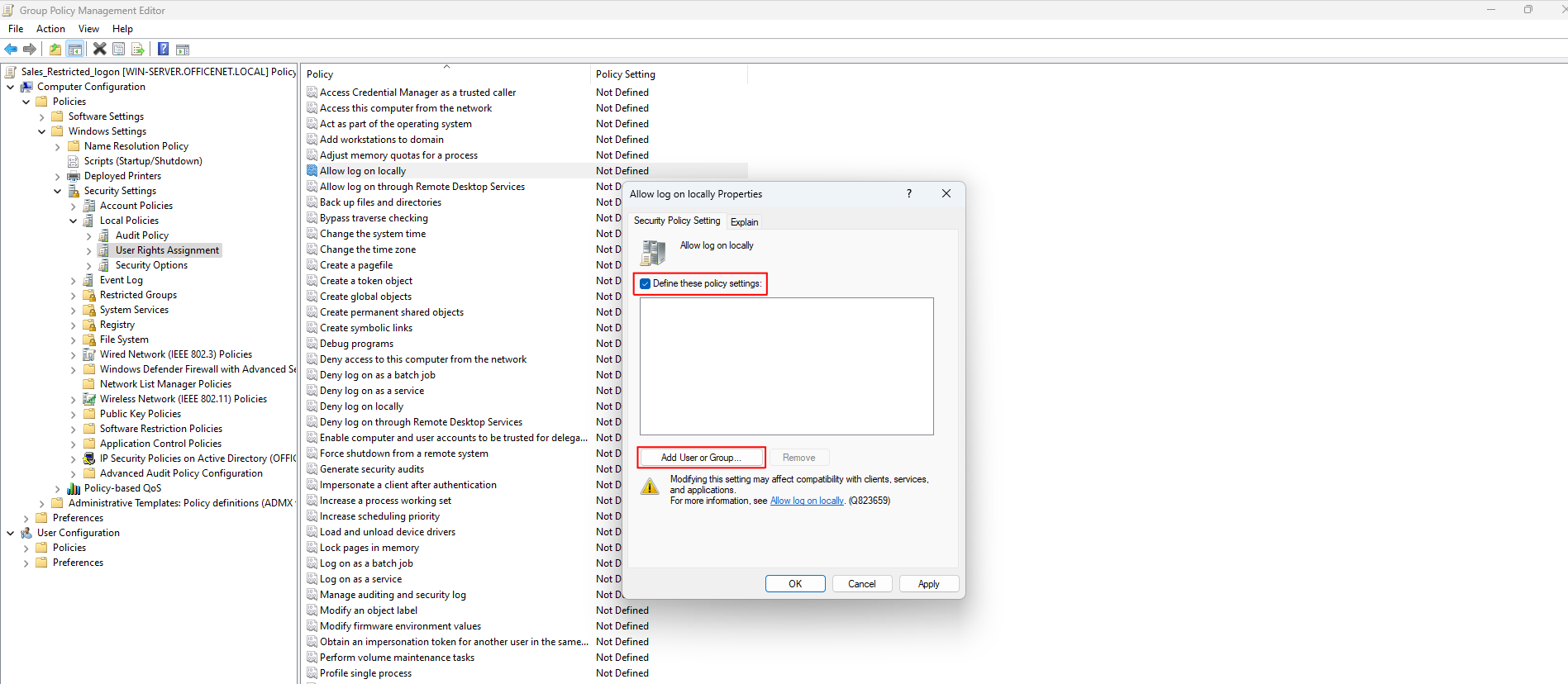
Make sure to check ‘Define these policy settings’ and then click the ‘Add User or Group’ button:
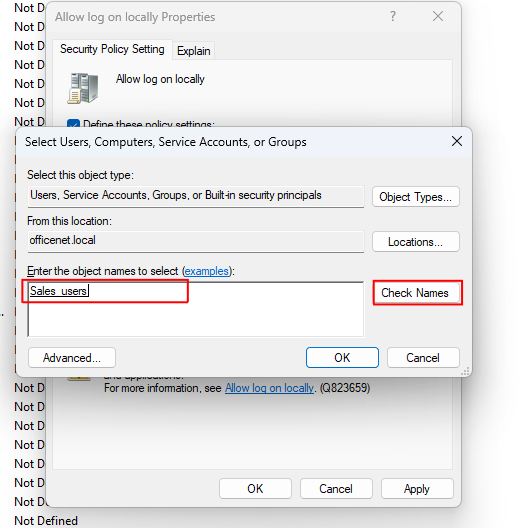
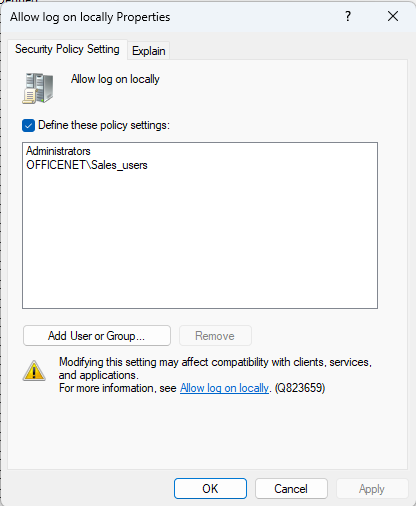
The easiest and quickest method is to type the group name and click the ‘Check Names’ button to verify it. Then hit OK. I will need to add the Administrators group as well:
Now I will force the machine to update its group policies. Open Powershell and type:
gpupdate /force
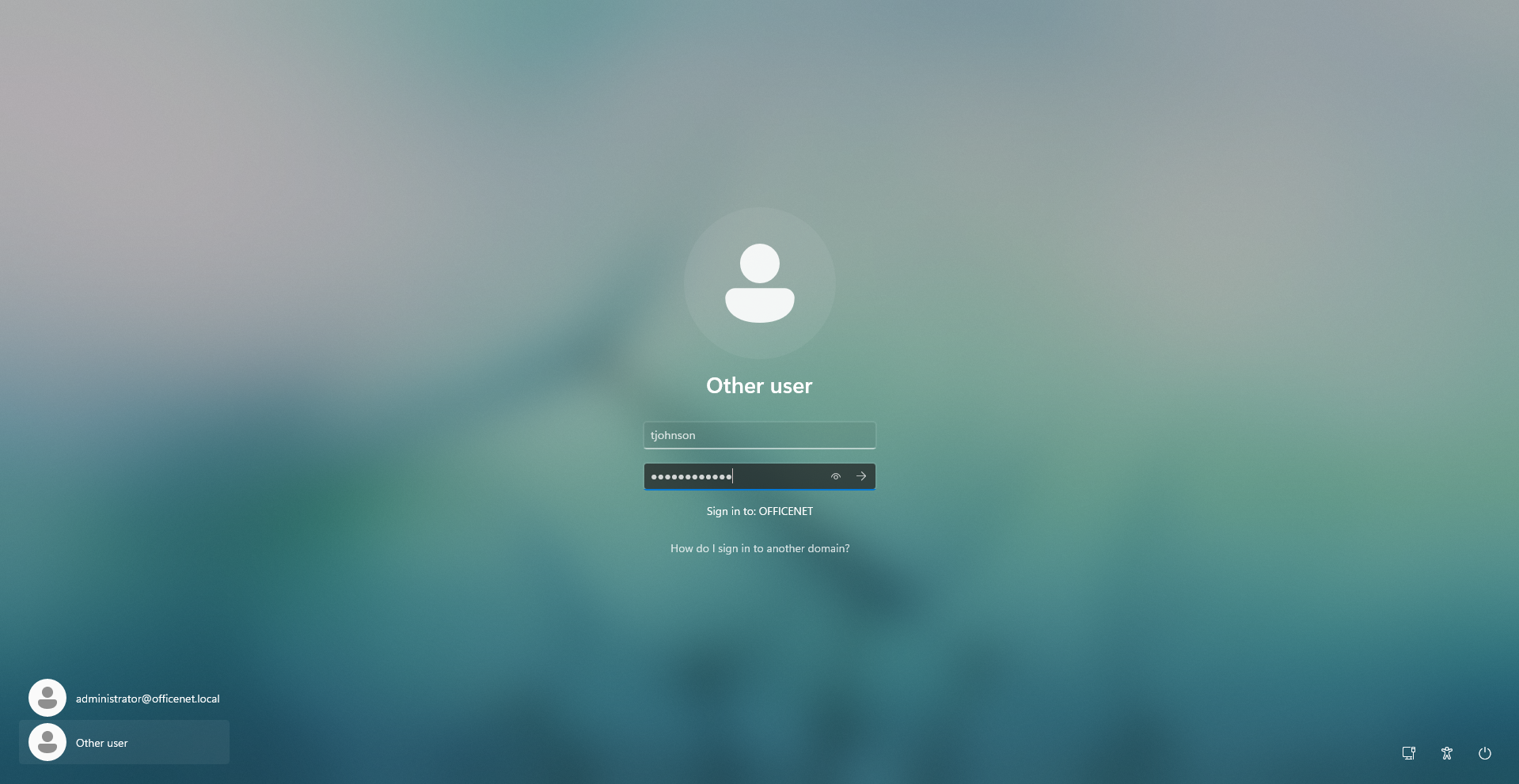
Finally, I’ll log out of the machine and try to login with a user that should no longer have access. I’ll try and login as Tina Johnson:
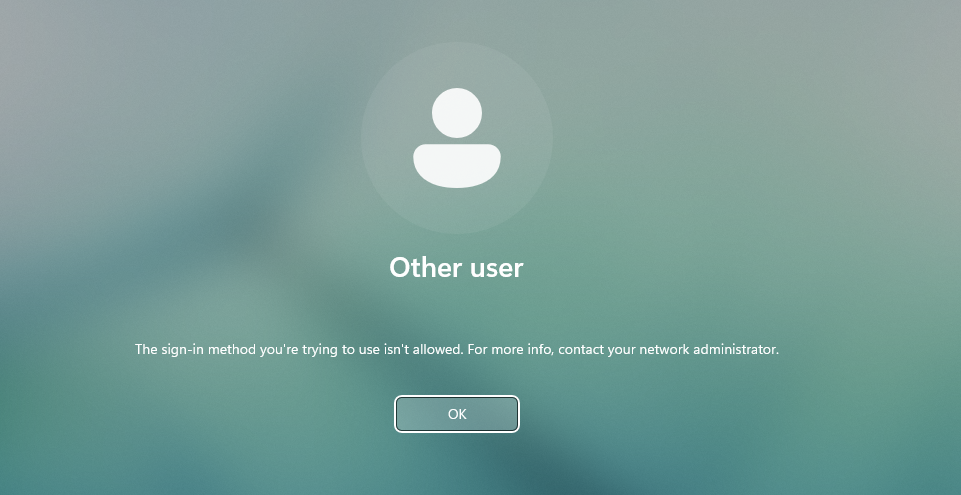
The machine is no longer allowing Tina to login:
It’s working as intended! I’ll need to repeat this for the other department OUs. Once done, when trying to login to the Development machine using the Sales user (Wolf Wallstreet) I’ll receive this response:
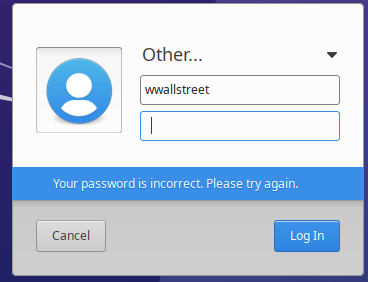
It is saying the password is incorrect even though I entered the correct one. The PC can no longer authenticate the incorrect user.
Perfect! Users are no longer able to login to machines that do not belong to their department.





